Insecure Software Is a Huge Industry Problem Because
Third-party software is a significant percentage of the enterprise software infrastructure and third-party components are a significant percentage of. Most software is indeed very insecure.

The Most Effective Methods To Overcome Software Vulnerabilities Specbee
The fragmentation of software development caused by the upsurge of companies embedding software into their products will compound this structural failure.

. The results of insecure software--cybercrime and cyber-espionage--are largely social costs not paid by the individual whos responsible for the behavior. Sensitive data exposure is a big problem in information security as exposed records are a major threat to the victims and your company. The problem with this process is that no one entity has any incentive expertise or even ability to patch the software once its shipped.
So in order to get programmers to write secure code as a first step we have to teach them how to do that. Second -- software is not sufficiently engineered to fulfill the role of foundation. And the automotive industry in particular is vulnerable to cyberthreats.
O All are true. Ssh -p pwd root1982540120. This is a huge problem.
Thats led to recalls in the medical device and automotive industries. You can have very strong password but the password is stored anywhere in the Linux logs now. What is happening right now because of world-wide interconnection of insecure software gives social problems once limited by geography a new destructive range.
O Many software professionals were not trained in security. No Microsofts code is insecure because people would rather buy a copy now than wait 6 months for a version with fewer features because it is more secure. Neuberger while acknowledging the clear influence of SolarWinds on the cyber EO pointed to a broader concern and suggested a wider societal approach to.
How come our security expert making 100000 will write something like that. OpenGlobal has always been a big advocate of open source software mainly for the technical advantages that it brings but the price ie usually free is also a nice incentive. Insecure software is making us fragile vulnerable and weak.
It is really not about that programmers would refuse to do so. Vulnerabilities lead a consumers computer. But Ive recently heard of a web designer advising clients against open source because it is inherently insecure due to its public nature.
Geekonomics has 3 main themes. Cyberattacks against embedded systems could lead to wide-scale damage to. Old tech is a problem that the industry as a whole has done very little to address and the problems are going to get a lot worse over the coming years before theres any sign of things getting.
The highest problem of the software security is poor knowledge of responsible people about security. Geekonomics focuses not on the code but rather how insecurely written software is an infrastructure problem and an economic issue. The WWW is fun but static.
When using tools like Amazon S3 never make a bucket publicly available. To make matters worse its often impossible to patch the software or upgrade the components to the latest version. The reason is that its hard to make computers both useful and secure.
So we start adding features and capabilities. Remember a product only needs to be as good as the customer is willing to buy. You make money in IoT at.
Some experts fear that nothing short of a digital Pearl Harbora large-scale attack that exploits critical security holes in our industrial. Generally speaking the term software security is used to denote designing building testing and deploying software so as to reduce vulnerabilities and to ensure the softwares proper. Microsofts code is insecure because this way customers can be made more dependent on them.
And the software is old even when the device is new. Insecure software is a huge industry problem because There is little financial incentive to implement security in software O Software products are often rushed to be released. First the cost of IoT devices and associated profit margins are really small.
You can make them completely secure by disconnecting them from the internet and taking other measures but then they arent so useful. The problem is that they lack the necessary secure coding education and they what kind of bugs hackers exploit and therefore they do not know how to prevent them. O Security is hard to measure.
Becky Bace The Real Cost of Insecure Software In 1996 software defects in a Boeing 757 caused a crash that killed 70 people In 2003 a software vulnerability helped cause the largest US. I think there are a couple of reasons. Cyber criminals terrorists and.
This is not the default for S3 buckets so a person has to consciously make the effort to expose an S3 bucket publicly. We connect our PCs to the internet. First -- software is becoming the foundation of modern civilization.
The economic and legal structure of the software development industry leaves no single entity with strong enough incentives to secure software before it is shipped. The threat of global warming might be on everyones lips and the polar ice caps might indeed melt but not for a time. Critical infrastructure including power generation oil and gas refining.

Pdf Effects Of Software Security On Software Development Life Cycle And Related Security Issues

Pin By Vika On Trendy2019 Blockchain Blockchain Technology Technology

Fine Dining Marketing Framework Infographic Event Marketing Plan Infographic Fine Dining

Pdf Measuring The Cost Of Software Vulnerabilities

Labour Hire Management Software Entirehr In 2020 Workforce Management Software Hiring

Teamviewer 14 1 18533 0 Blackberry Os Key Software Support

Securing Software Supply Chains And Dependency Confusion An Industry Perspective

Pdf Measuring The Cost Of Software Vulnerabilities

Pdf Security Risks In The Software Development Lifecycle

The Blockchain Enabled Intelligent Iot Economy Blockchain Blockchain Technology Technology

How Your Business Can Proactively Protect Customer Data Infographic Infographic Business Data
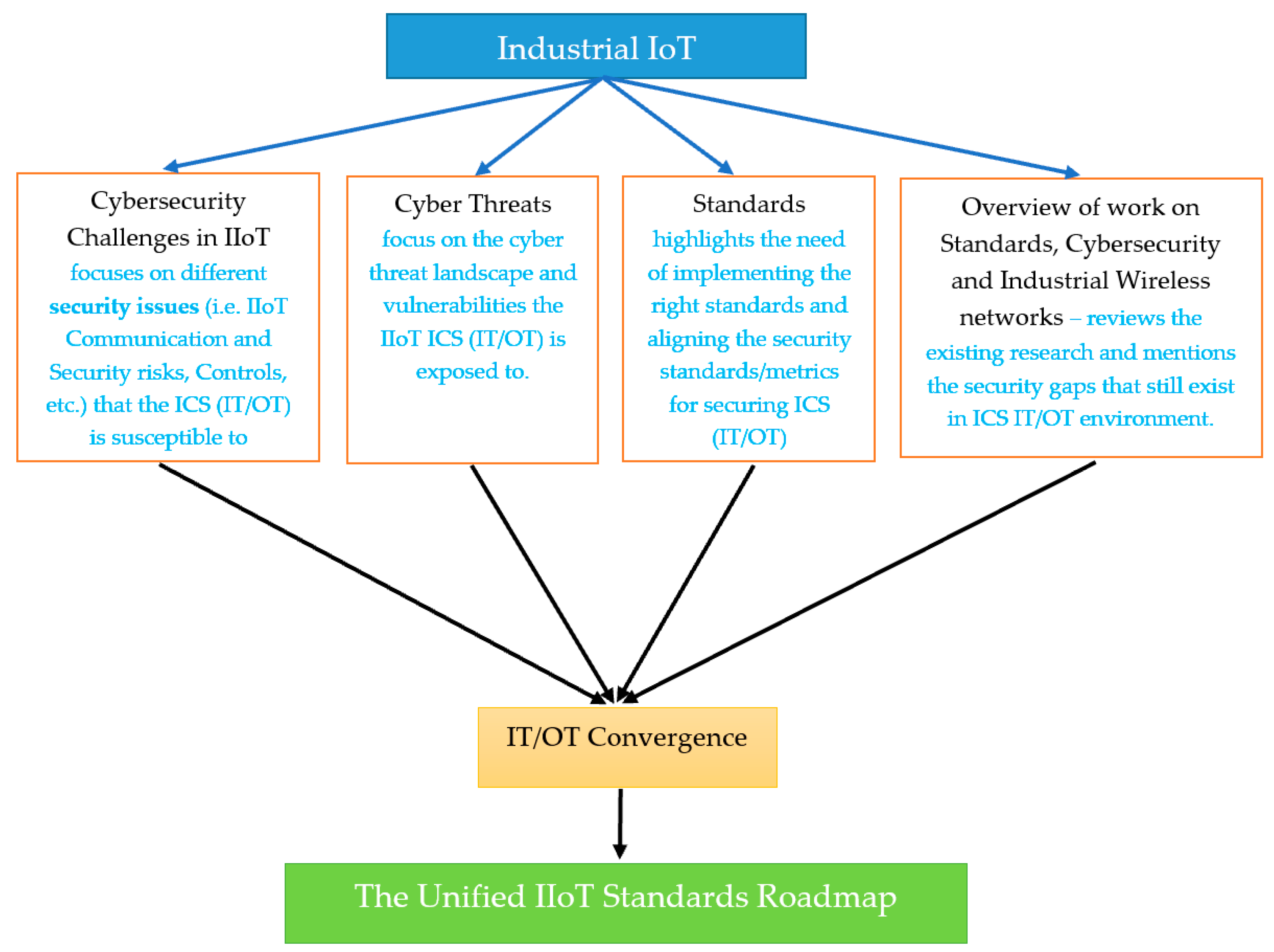
Sensors Free Full Text Industrial Iot Cyber Threats And Standards Landscape Evaluation And Roadmap Html

2022 Software Security Predictions That Should Be On Your Radar Synopsys
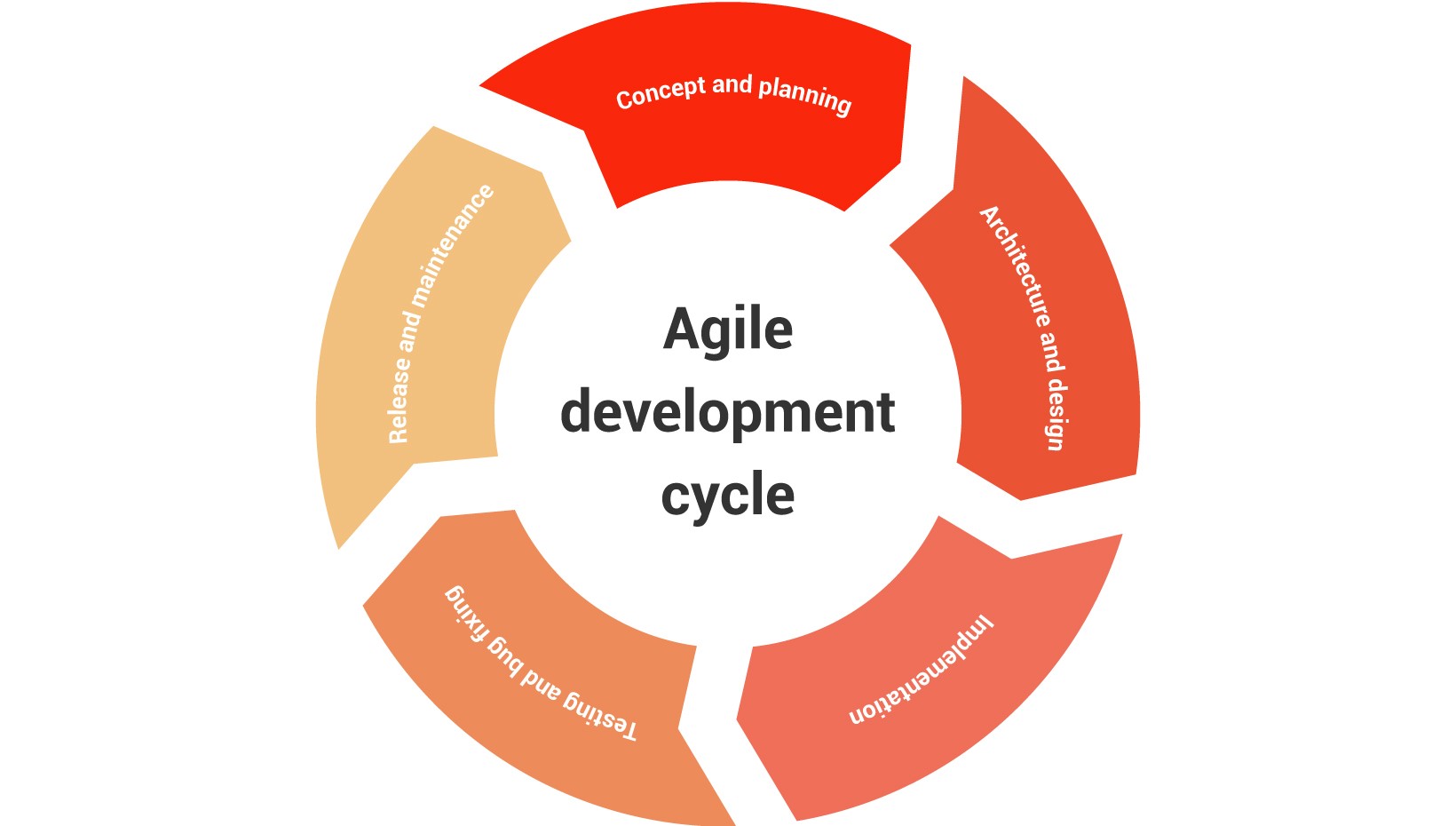
Secure Software Development Best Practices And Methodologies For Secure Sdl Lifecycle

How To Achieve Application Security With A Secure Software Development Lifecycle Sdlc Iosentrix

5 Core Criteria For Selecting Software Development Company Software Development Development Company Portfolio

Pdf Systematic Mapping Study On Security Approaches In Secure Software Engineering
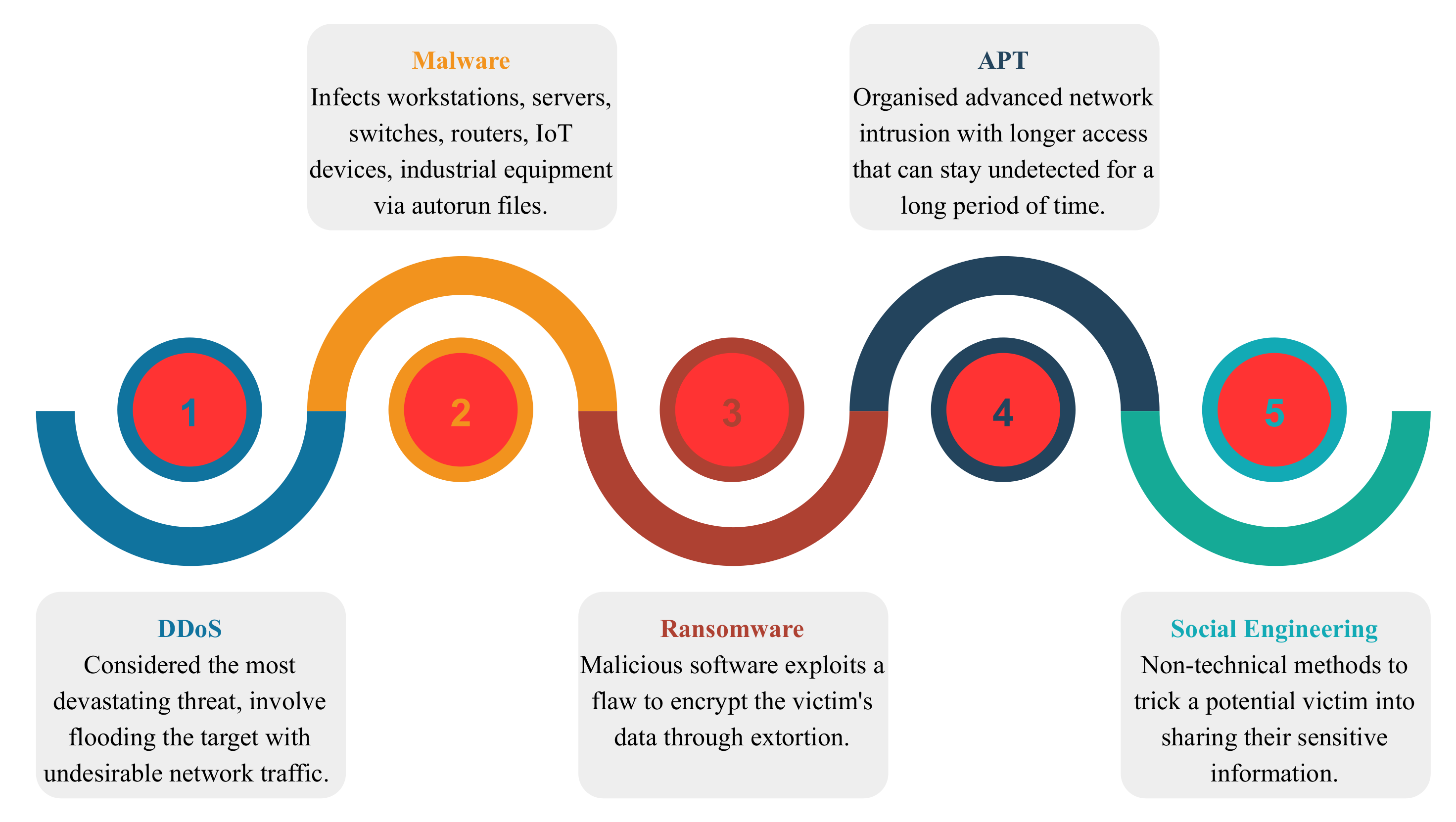
Applied Sciences Free Full Text Internet Of Things Meet Internet Of Threats New Concern Cyber Security Issues Of Critical Cyber Infrastructure Html

Comments
Post a Comment